With over 64 million websites using WordPress as their CMS, it comes as no surprise the number of security attacks that can happen to websites using WordPress. It is a lot.
If you had ever run a WordPress website for a good amount of time, you must have surely seen spam comments and attacks on it. It is either the spammy commenting techniques or injecting code in your forms.
WordPress website is not easy to hack when you are using it in its basic mode. That is the basic WordPress installation. Since WordPress is an open-source platform, it also invites developers to be creative and create their own themes and plugins.
The WordPress themes and plugins can be designed and developed in different ways. This is where the hackers take advantage and try to find a security breach with the websites that use open source themes or plugins.
WordPress websites that use premium plugins but downloaded from other warez sites or free download sites are at risk too. A lot of free download sites have malware encoded into the theme or plugin.
There are many ways a WordPress website can be attacked. It can be either a simple code injection attack or a complete website takeover.
In today's post, we are going to talk about the problem of WordPress redirect hacks. Is your WordPress site redirecting to another site when you try to login to the admin dashboard or visit some of the popular pages of your site? Then this post is for you.
WordPress Redirect Hack Fix
If you are sure that your website is redirecting to spam. Then it is time to fix it. But first, let's try to do basic research on what caused this spam redirect and how bad it is.
The malware redirect of the website can be caused by code injections in website comments, forms, or user registration/login pages. It can either be a code injection or SQL injection to these open-ends of your WordPress website.
Check WordPress Website Files
If the website or parts of it like the admin dashboard or login pages are redirecting to spam, then it gets difficult to find the cause of this redirect hack.
So we will directly get down to fixing it by inspecting for any suspicious files on your website hosting server. Open your FTP application that you use to upload your files, check if the public_html or htdocs folder of your website looks like this:
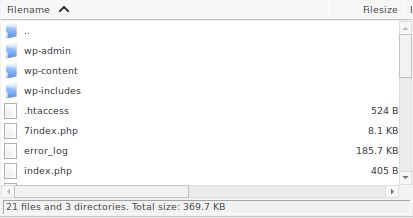
Check if there are any weird name files there. Also, check the “Last modified” column of the FTP connection.
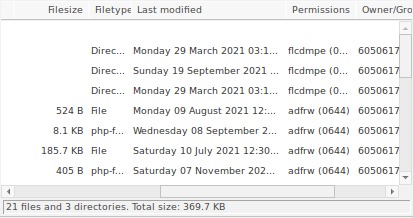
See if any of the files have been recently modified. If so, then download and open it to check for any weird code.
Similarly, keep checking for new files in the wp-admin and wp-includes folder. Note that I haven't spoken about the wp-content folder.
This is because, if you have any new files injected in these two folders, then probably your website has more serious issues to look into. You need to check the files and folder permissions of your website.
Now go into the wp-content folder of your WordPress website and then check for any new files and folders.
wp-content folder of your WordPress is where the uploaded files and images are stored. So there can be many files and folders with the latest timestamp in the “Last Modified” column.
Search for any new files in plugins and themes folder inside wp-content folder. Then move to the uploads folder, this is an important folder. Search for any weird named files or images inside it.
If there are any new files, try deleting these files in any part of your website's files. Check your website after deleting these new files for any redirect error.
If there are no new files, or the WordPress redirecting to the wrong URL then it is time to check for website database code injection.
Check WordPress Database For Hack
The usual places where the hacks inject code are either in the wp_posts and wp_options table.
Malicious scripts injected can be used to affect the wp_posts table of your WordPress database to redirect all the pages and posts of your website to be redirected to the spam website. Check all the posts in this table for any weird code.
Next, check the wp_options table, check the siteurl value. This is the place that needs to be changed for website spam redirect.
Other ways to check for WordPress hacked redirect malware
Google search
Search for your website in Google. If the Google bots have already found your website spam redirect, then the results for your website will have a “Site may be hacked” tag to them.
It is the way of Google to warn its users about the dangers of visiting your website. Also, something that can be useful for us.
Google Search Console
If you have added your website to the Google search console, then log in to the GSC dashboard. If there is a security issue, then the “Security Issues” tab will be visible.
Check this security issues tab for the affected URLs. This will give you an idea of how much of your website is affected.
Online Malware Scanners
There are many websites that can help you scan your WordPress website for malware redirect. We have written a complete post about it in our blog. Do check it out.
This post also shows ways to fix it by using WordPress plugins. But since you are having a redirect error. Use the online malware scanners that scan for free and they will give you the affected pages of your website.
Fixing the WordPress site redirecting to spam
It is always a good practice to keep your WordPress website backed up. We are assuming that you have a backup already on a different location than the affected server.
WordPress Plugin Backup
If you have used any plugin to backup your website, then go to its location now. It is time to fix the WordPress website redirect hack.
Download your backup files and extract them on your computer. Make sure this backup is not new but at least 30 days old. Or if you know the exact time since the WordPress redirect hack, then get the backup older than this date.
Compare the files in the backup you just extracted to those on the server. If you see any suspicious files present on the server that are not in the backup, download these files in a separate folder.
Open this new suspicious file and check for any encoded script or code. This will take some time but it is worth it.
If there is no new file or no suspicious files, then it is time to check the database file from the backup folder. It usually ends up with a .sql extension.
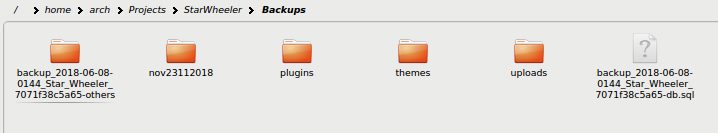
As you can see in the above image, the backup file is named with the domain name and date. It ends with a .sql file.
Open it and check the wp_posts and wp_options table.
Now go to your WordPress website's database table and check if the values of wp_posts and wp_options table match with the backup file.
In most cases, the culprit that causes the website redirect to spam is hidden in database tables. Because SQL injection attacks are the easiest attacks performed through website forms or outdated plugins.
If you haven't found any new files in your website files on the server, then it is most probably a database injection that is causing the website spam redirect.
To restore the database backup on your server, WordPress has an official guide here: https://wordpress.org/support/article/restoring-your-database-from-backup/
Website On AWS EC2 servers with RDS database
If you forgot to backup your website with a plugin or manually, then it is very difficult to recover from this spam redirect. But there is still hope if your website is hosted on AWS EC2 with database hosting on RDS.
If your website is structured like this where the files are on the EC2 server and the database is on RDS, then you are in luck. The good thing about RDS servers is that it keeps 10 days backup of your database.
Go to your RDS dashboard > Automated backups and select the database of your website.
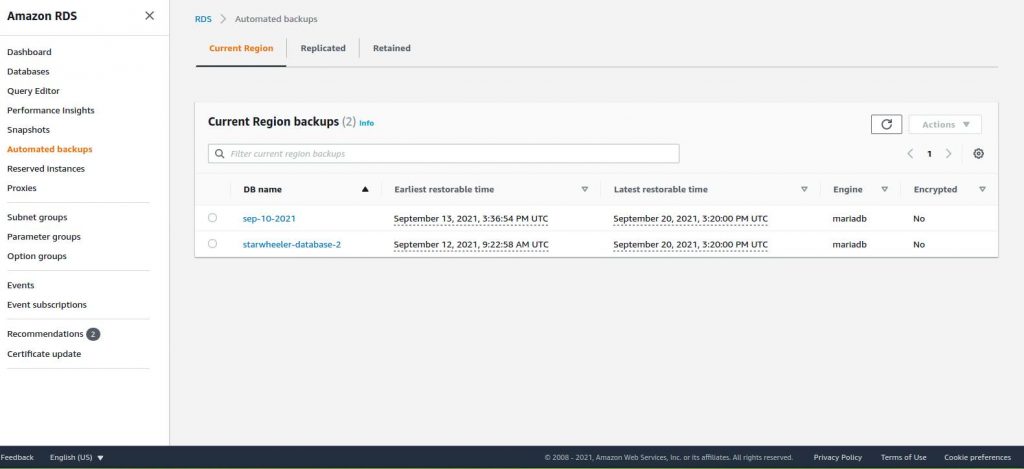
Scroll down and you should be able to see all the automated backups Amazon RDS has done for you.
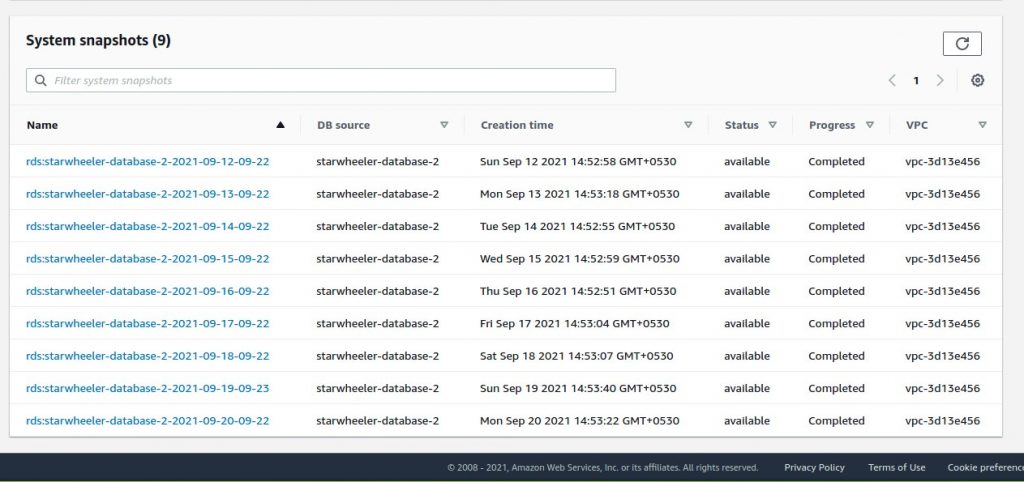
If you can estimate the date when your site was hacked or the date you last checked when everything was fine then it will be helpful. At the end of the database backup name, you will see the dates when that backup was done.
Select the date when everything was working fine or just a date before the last check when everything was fine. This will only work if that date is within the last 10 days.
Now on the right top, click on the Actions button and Restore snapshot. This will redirect you to the page of DB specifications.
Most of the things are auto-filled by Amazon itself. Make sure the “Existing VPC security groups” are filled right.
The “DB Instance Class” option has to be set right too. Select the right database size server which you were using before.
Click the “Restore DB Instance” button. After a few minutes, the new instance will be created.
Once the new DB instance is created, click on it and copy the Endpoint address.
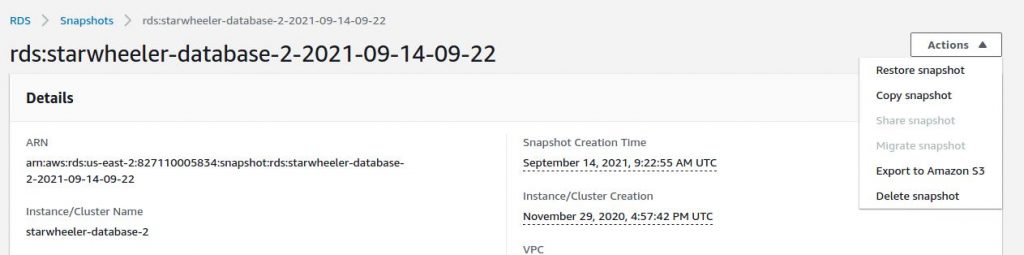
We will use this new endpoint address in the wp-config.php file.
Paste the new endpoint address by opening the wp-config.php file in the DB_HOST option. It should look like this:
define( 'DB_HOST', 'endpoint URL here' );Now go to your browser and check your website. Everything should be fixed now.
All the WordPress redirect to spam must have been fixed with this database restore.
Final Words
Removing malicious redirects from the website is a tedious and difficult task. A good level of server management and database management skills is required.
Make sure your team is up to that level or hire a good team like UnderWP. We try our best to fixing WordPress errors like these redirect hacks.
Once your website is back to normal, make sure to check for any outdated themes and plugins. Update your WordPress and its themes and plugins to keep it secured in the future.
If you know any other ways to recover from a website redirect hack, do let us know in the comments.



Great post. This was very helpful. My wp_options table was inserted with the new spam URL. Thanks to this post I was able to fix it without any loss of data.
Helped me remove malware from my website. Thanks.
scanning database tables helped me remove malware that was causing a spam redirect on my website. It created new database tables that were not associated with any plugins. Searching the database table names on Google and not finding any plugins related to it helped me find the malware.
AWS has option to set automated backups. Did not know that until I read this post. Thank you for helping me find this AWS service.
I think enabling this option, it will help you recover your website if the malware attack happened in less than a week. Online monitoring tools will not help in this case as well because they check only the online availability of the website. When a malware attacks, the website will be still online but redirecting to somewhere else which is undetectable. Always checking your website once in a week helps I say.